While most modern smartphones can do almost everything a computer can, sometimes a larger screen is necessary. Many may think that Windows or Macs are the only computers you should buy. However, Chromebooks are a great option for most people. They are often more affordable, do much of what a Microsoft Windows or Mac device can do, and have access to Android apps and Linux. There’s also a variety of great Chromebooks at multiple price points to meet consumer needs.
In addition to being good for consumers, Chromebooks are also a great option for businesses and schools. ChromeOS, the Chromebook operating system, has features to keep Chromebooks secure, such as automatic updates and verified boot mode. One of these features is Verified Access, which verifies whether a ChromeOS device is authentic. This guide discusses what Verified Access is and why it’s important.

How to use your Chromebook when you don’t have a Wi-Fi connection
An offline Chromebook can still use many of its cloud-based apps
What is Verified Access?
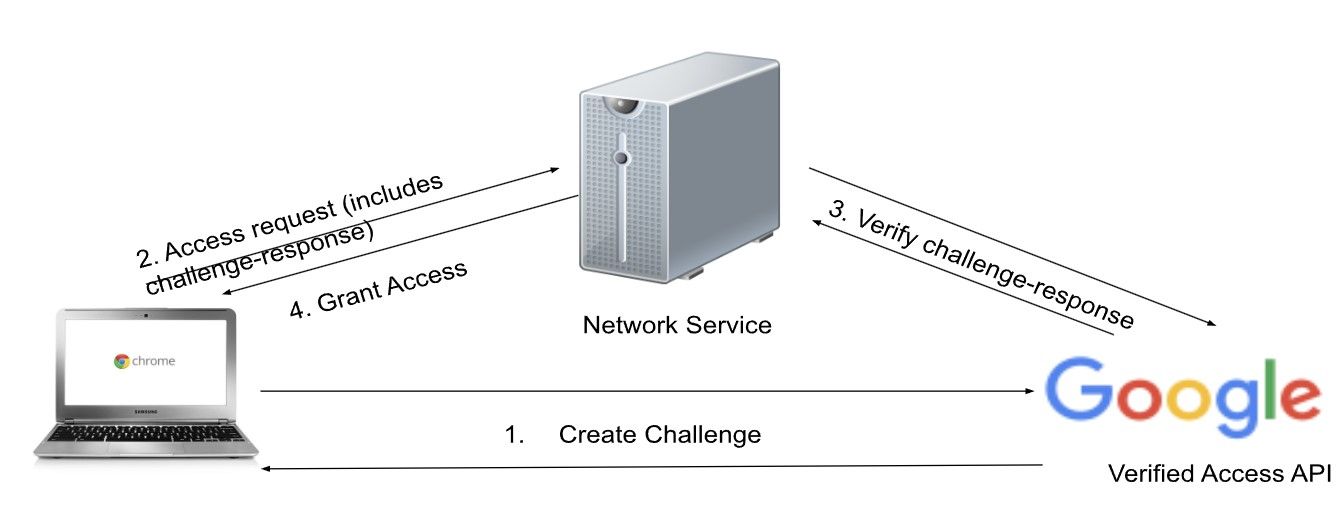
Verified Access is a security feature that verifies whether a ChromeOS device connected to a network or server is authentic and meets policy compliance. This authentication process occurs before a device can access the server or network it’s attempting to connect to. When a network service requires verification, the Verified Access API sends a challenge to your device. Depending on the challenge response, the device is allowed or denied access to the network.
Source: Google
This is useful for enterprise devices because they contain sensitive user data. By leveraging the TPM chip inside Chromebooks, you can make sure your devices are secure using hardware-backed verification without relying on clients. Administrators must allow Verified Access and create enterprise policies for the feature to work.
How do I set up Verified Access?
To leverage Verified Access, you’ll activate its functionality in the Google Admin console and force-install a Chrome extension on users’ devices.
1. Set up device enrollment in your domain.
2. Install a Verified Access app on the device. You can use a third-party extension or implement your own.
3. Set up an authorization endpoint. Use a VPN or Certificate Service extension to issue and verify certificate authority on each device. This service can be from a third party, or you can create your own.
4. Determine and create Admin console policies. Choose between device or user verification and set up application policies. User verification is the more secure option because it encompasses both device and user verification. Device verification lets anyone who accesses the device use the network since the device’s identity was verified.

How to fix a slow Chromebook with ChromeOS Diagnostics
Check out how each component of your Chromebook is doing
Keep your devices and enterprise secure
Chromebooks are great devices whether you’re a student, running a business, or using one at home. Verified Access keeps Chromebooks for schools or businesses secure by adding extra verification for devices to access sensitive networks. After setting up Verified Access, you can easily share files between devices with Nearby Share.
Source link