Summary
- Android 15 DP2 adds user authentication before changing USB modes, enhancing device security against unauthorized access.
- The new feature prevents potential data theft by requiring user authentication via PIN, biometrics, or password.
- Leaving Developer Options on could still pose a risk of unauthorized data transfer, highlighting the importance of device security measures.
We’re still months away from the stable release of Android 15, but we’re starting to get a better glimpse at what to expect in the new OS version thanks to preview builds shared by Google. While the latest developer preview released by Google mainly includes new APIs and behavior changes that are relevant to app developers, it also packs some new user-facing changes that are worth noting. For example, the second DP brings the Swipe up to continue feature that we’ve been waiting for on the Pixel Fold. It also adds a simple, yet welcome security feature: a requirement to authenticate the user before changing USB modes.

Android 15: News, leaks, timeline, and everything new
Here’s what we know about Android 15 now that the first developer preview has landed
As of Android 14 QPR1, the OS supports 5 different USB modes: “File transfer/Android Auto” (MTP), “USB tethering” (NCM), “MIDI”, “PTP”, and “Webcam” (UVC). Starting in Android 15 Developer Preview 2, you’ll need to authenticate yourself via your lock screen PIN/password/pattern or via your biometrics before you can change USB modes. In previous releases, you didn’t need to pass any authentication challenges to change the USB mode, though you did need to unlock the device in the first place in order to access the USB preferences page.
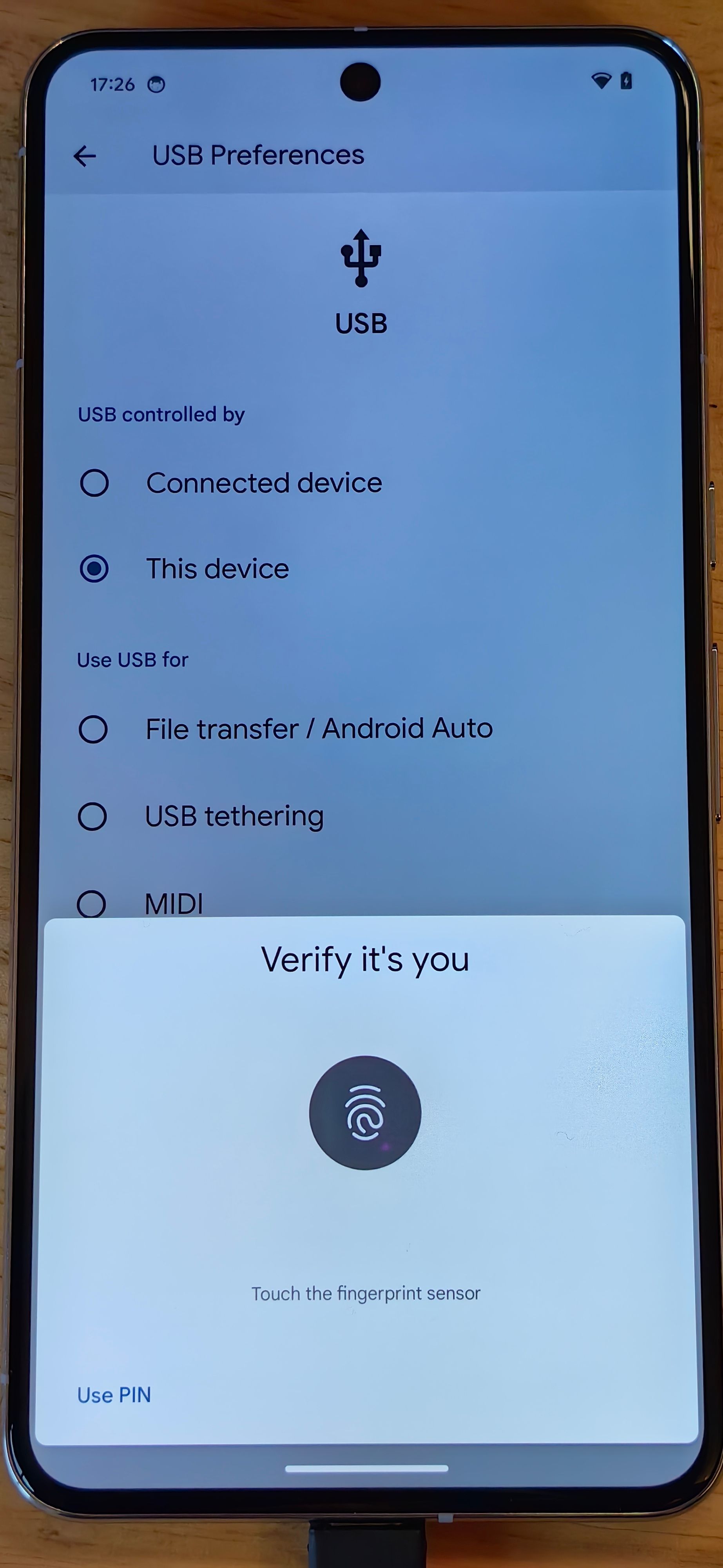
It’s a big security improvement, but there’s still a small loophole
It might not immediately make sense why Google is adding this additional step to change USB modes. The reason is that there’s no guarantee that the person who’s trying to change the USB mode is actually the owner of the device. They could be someone the owner handed their phone over to or, potentially, a thief. That’s why Android already requires authentication when changing or accessing certain settings and why many apps utilize the BiometricPrompt API before proceeding with certain operations.
One thing to note: If you leave Developer Options on, then it’s possible for someone else to enable USB debugging, connect your phone to their PC, accept the USB debugging authorization on your phone, and then dump all your files onto their PC. Thus, if you want to really make sure that someone else can’t easily dump all your files, then you should consider leaving Developer Options off. Google could solve this by fully disabling USB data signaling when the “no data transfer” mode is enabled, a feature that was added back in Android 12. Admittedly, it’s a niche solution to a niche problem, but Android is used by billions of users, so cases like these are bound to arise.

Android 15 DP2 arrives ahead of next month’s open beta: Here’s what’s new
Better satellite connectivity and NFC. plus more apps for the cover screen on flip-style foldables
Source link

