Ransomware attacks affect everything, including healthcare facilities, pharmaceutical companies, tech firms, and hotels and casinos in Las Vegas. Ransomware has reached a record high, with payments exceeding $1 billion in 2023. Why is this malware so notorious? The name “ransom” immediately gives it away. You might be concerned about this malware on your Android or computer. Here’s all about ransomware and how to protect yourself so no one can extort you using your high-end Chromebook.

Can Chromebooks get viruses?
Here’s what you need to know about viruses, malware, and your Chromebook.
What is ransomware?
Ransomware is malicious software (malware) that infiltrates computers and restricts access, holding the system hostage until a ransom is paid. This kind of malware has been around for several years. The AIDS Trojan has a storied past that stretches back to 1989, long before the widespread use of the internet for disseminating malware.
Ransomware tries to force victims to pay by displaying an on-screen message. These alerts often indicate that the system has been locked or files encrypted, warning that access will remain blocked without a ransom payment. The amount requested can vary and is usually demanded in a virtual currency like Bitcoin to obtain a decryption key.
Types of ransomware
Ransomware has evolved over the years, with different characteristics and attack methods.
Encryptors
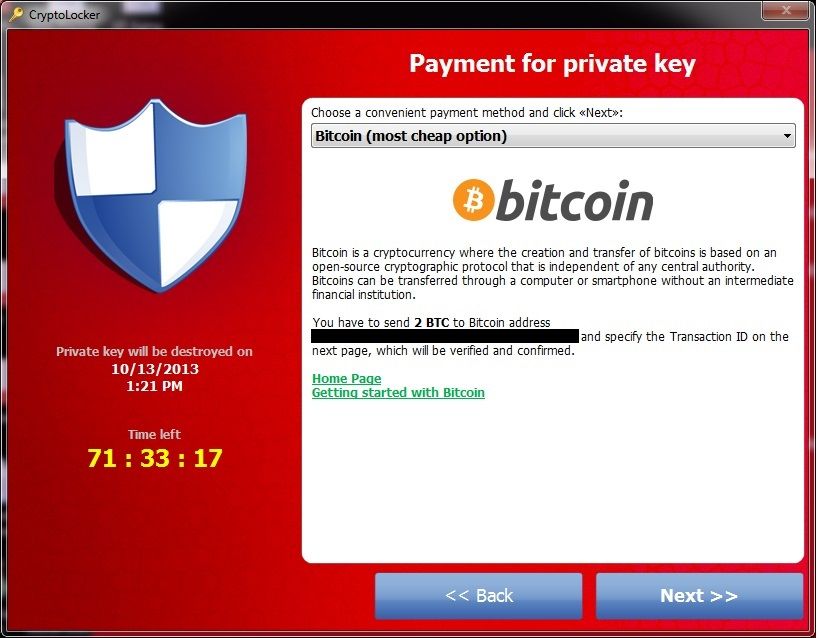
This is the most common form of ransomware. It encrypts the victim’s data and files using strong encryption techniques. Attackers then demand a ransom in exchange for the decryption key. Noteworthy examples of this type include WannaCry and CryptoLocker.
Source: Avast
Lockers
Locker Ransomware takes a different approach than encryptors. It doesn’t encrypt files. Instead, it locks the victim out of their device. Victims find themselves locked out from their files, applications, and system settings, with a ransom message appearing on the screen.
Scareware
This ransomware acts like bogus antivirus or cleaning tools. It bombards users with pop-ups and phony threat notifications, insisting that paying a fee will clear up any issues. Although it’s not as damaging as encryptors or lockers, it can be irritating and sometimes includes threats to delete files.
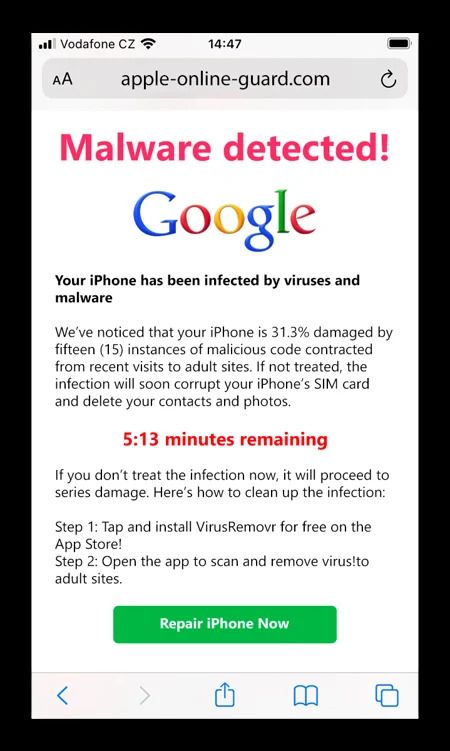
Doxware or Leakware
In Leakware scenarios, rather than erasing data, the attacker threatens to make it publicly available. Also called Doxware, these attacks primarily target organizations such as banks and government agencies, which manage susceptible information.
RaaS (Ransomware as a Service)
In this model, ransomware creators monetize their software by selling or leasing it on the dark web, allowing other affiliates to carry out attacks. The resulting profits are divided between the malware creators and the attackers.
Double extortion
This is a more aggressive tactic where attackers do more than encrypt data. They also steal it. They then threaten to publicly release the stolen data if the ransom isn’t paid, even if the files are decrypted. This tactic increases the pressure on victims, compelling them to comply.
Triple extortion
Triple extortion ransomware takes the concept of double extortion one step further by introducing a third layer of coercion. This often involves demanding a ransom from the victim’s business partners or customers or escalating their attacks with a distributed denial-of-service (DDoS) against the victim’s company.
Common ransomware attack patterns
Familiarity with the frequent strategies of these attacks is important for setting up effective defenses and reducing risks. Here’s a rundown of common attack patterns.
Phishing attacks
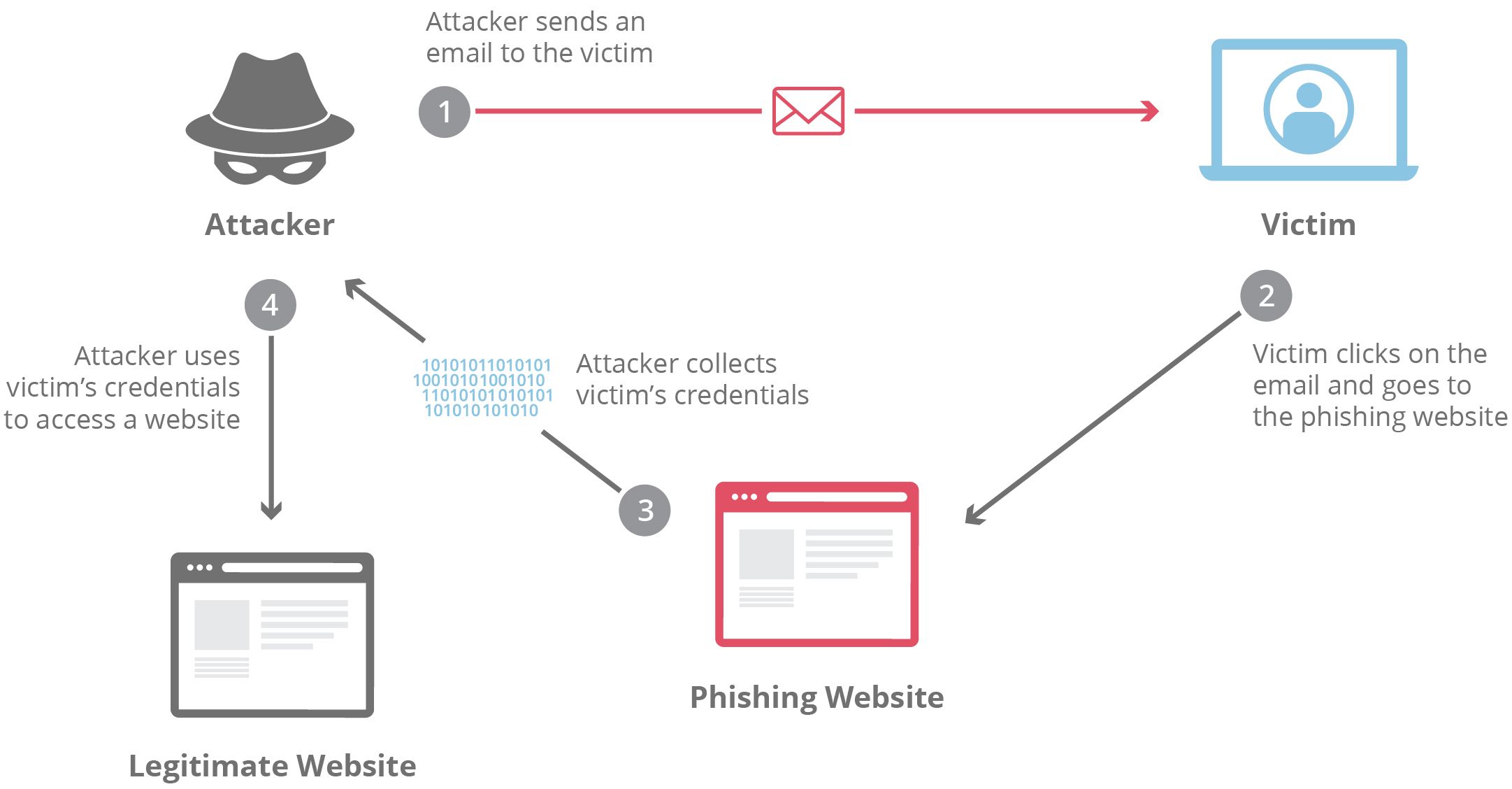
According to a study by Deloitte, 91% of cyberattacks start with phishing and spear phishing messages. Hackers prefer these techniques to sneak ransomware into systems. They typically prepare by researching their targets thoroughly. Afterward, they send persuasive emails with hazardous attachments like ZIP files, PDFs, and spreadsheets with embedded malware. These emails may also contain links to deceptive websites cleverly designed to deceive you into downloading ransomware that threatens to compromise your network.
Source: Cloudflare
Malicious ads
Malicious advertising, also known as malvertising, is increasingly used to distribute ransomware. Hackers purchase real advertising space in this scheme and link it to an exploit kit. When you click these ads, the kit scans your system for details like operating system, software, and browser specifics. It tries to deploy ransomware on your computer if it finds a vulnerability.
Using pirated software
Pirated software and software bundled with adware are pathways for ransomware entry. Users who engage with pirated software increase their risk of ransomware attacks and miss crucial security updates due to not receiving official software patches, making them more vulnerable to such attacks.
Portable computers and USB drivers
Laptops are often at risk of ransomware attacks since they typically store large amounts of sensitive data and are integral to our daily work. Similarly, USB drives are a favored tool for delivering ransomware. Their ease of transportation and ability to connect to various computers make them particularly effective.
When a malware-laden USB drive is inserted into a computer, it automatically executes the malware, infecting the system and potentially spreading ransomware to all devices on the network.
Public Wi-Fi
Public Wi-Fi is a common hiding spot for ransomware. When you access sensitive information in public spaces (think the local Starbucks), consider switching to secure 4G or 5G access or using a VPN to protect your data when working outside the office is unavoidable.
Best VPNs for multiple devices in 2024
It only takes one of these VPN subscriptions to cover your whole fleet of computers, mobile devices, and streamers
How to defend yourself from ransomware
Prevent ransomware and minimize damage by following these simple steps.
Back up your data
The most effective way to protect against the loss of critical files is by maintaining backups, both in the cloud and on an external drive. Shifting your data to a cloud service simplifies and secures the backup process against potential threats. If ransomware infects your system, wipe your device and restore your files from these secure backups.
Ensure the systems where you keep your backups can’t change or delete them. Ransomware actively seeks out backups to encrypt or delete them, rendering them unrecoverable.
Use security software and update it regularly
Keep all your computers and devices secure by installing robust security software, and don’t lag behind on software updates. Regular and timely updates are key to protecting your systems against the latest threats.
Protect your digital life
Being cautious is your best defense. Think before you tap or click. Don’t respond to emails and text messages from unfamiliar contacts. Plus, restrict your app downloads to trusted sources and use safe browsing. This simple precaution can save you from unnecessary security risks.
Source link